Configuring Dual-CE BGP High Availability Site. This article provides Juniper Configuration Example that uses BGP AS-Prepend to identify primary and secondary paths.
Introduction
The goal of today’s exercise is to build a High Availability (HA) Site that would be dual-homed to different PE routers of the same upstream Internet provider. This is one of the common scenarios described in BGP for Enterprise Networks article. As you might recall, dual-homing to the same ISP does not require your company to acquire Public BGP AS and Provider Independent Internet-Routable IP Space, while providing protection against single link and/or CE failure.
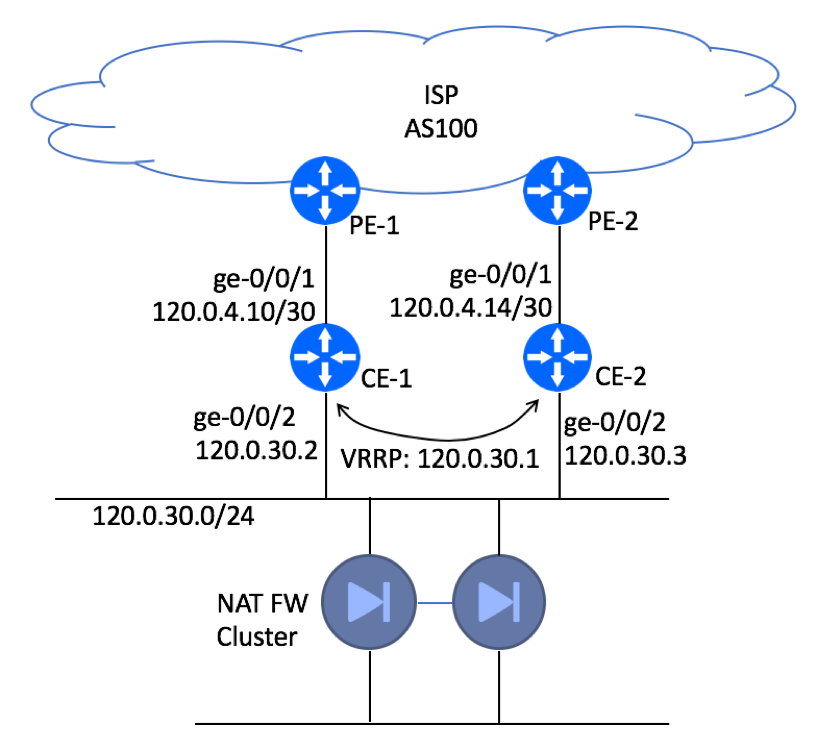
Physical Topology Diagram
In our example, we will build the topology with two CE devices that will run VRRP between them. CE-1 to PE-1 link will be designated as the primary path, CE-2 to PE-2 will be used in case of the primary link failure.
BGP Logical Diagram
BGP Logical Topology for the dual-homing scenario is displayed below. EBGP sessions will be setup between CE and PE devices with IBGP session between two CEs.
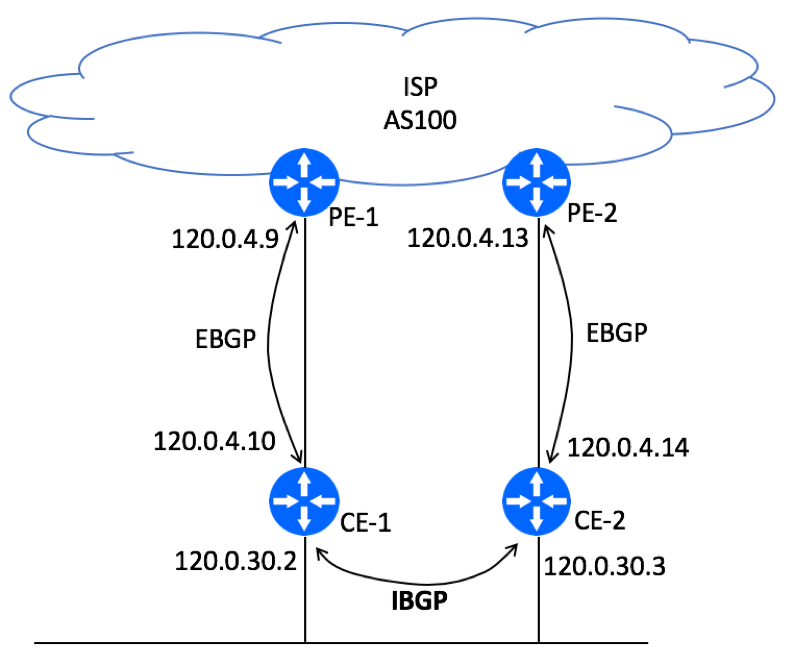
As mentioned earlier, CE-1 to PE-1 link will be designated as the primary path. In order to avoid asymmetric traffic flow (packets leaving the network via one CE but returning via a different CE), we need to make sure that CE-1 will be the preferred router for both Ingress and Egress traffic.
In order to take care of the Egress traffic (customer site to ISP direction), CE-1 will be setup with a higher VRRP priority. We will also setup higher local preference (120) for the default route received via CE-1.
For Ingress traffic, we need to find a mechanism to tell the ISP that routes received from CE-2 should be inferior to those received from CE-1. This can be achieved by either advertising special communities that are understood and supported by your ISP, or using AS-Prepend on CE-2 – PE-2 path. We’ll use the latter AS-Prepend approach, as it is universally supported by the majority of ISPs.
BGP Configuration and Verification
EBGP Session between CE-1 and PE-1
- Configure AS Number and Router ID
set routing-options autonomous-system 65001 set routing-options router-id 120.0.30.2
- Configure EBGP Session and Accept Default Route with LP=120 while rejecting all other prefixes
set policy-options prefix-list Default 0.0.0.0/0 set policy-options policy-statement Default term 10 from prefix-list Default set policy-options policy-statement Default term 10 then local-preference 120 set policy-options policy-statement Default term 10 then accept set policy-options policy-statement Default term 999 then reject set protocols bgp group ISP-AS100 type external set protocols bgp group ISP-AS100 import Default set protocols bgp group ISP-AS100 authentication-key "$9$9UPDt0IylMNdsEcds24DjCtu" set protocols bgp group ISP-AS100 peer-as 100 set protocols bgp group ISP-AS100 neighbor 120.0.4.9 description "ISP FastAccess: Circuit GD8AJ12B: ISP NOC 800-111-2222"
- Advertise Network Prefix to ISP
set policy-options prefix-list LocallyOriginated 120.0.30.0/24 set policy-options policy-statement Direct-To-BGP term 10 from protocol direct set policy-options policy-statement Direct-To-BGP term 10 from prefix-list LocallyOriginated set policy-options policy-statement Direct-To-BGP term 10 then accept set policy-options policy-statement Direct-To-BGP term 999 then reject set protocols bgp group ISP-AS100 export Direct-To-BGP
EBGP Session between CE-2 to PE-2
- Configure AS Number and Router ID
set routing-options autonomous-system 65001 set routing-options router-id 120.0.30.3
- Configure EBGP Session and Accept Default Route with LP=100 while rejecting all other prefixes
set policy-options prefix-list Default 0.0.0.0/0 set policy-options policy-statement Default term 10 from prefix-list Default set policy-options policy-statement Default term 10 then local-preference 100 set policy-options policy-statement Default term 10 then accept set policy-options policy-statement Default term 999 then reject set protocols bgp group ISP-AS100 type external set protocols bgp group ISP-AS100 import Default set protocols bgp group ISP-AS100 authentication-key "$9$9UPDt0IylMNdsEcds24DjCtu" set protocols bgp group ISP-AS100 export Direct-To-BGP set protocols bgp group ISP-AS100 peer-as 100 set protocols bgp group ISP-AS100 neighbor 120.0.4.13 description "ISP FastAccess: Circuit GD8AJ12C: ISP NOC 800-111-2222"
- Advertise Network Prefix 0.30.0/24 to ISP with Prepend
set policy-options prefix-list LocallyOriginated 120.0.30.0/24 set policy-options policy-statement Direct-To-BGP term 10 from protocol direct set policy-options policy-statement Direct-To-BGP term 10 from prefix-list LocallyOriginated set policy-options policy-statement Direct-To-BGP term 10 then as-path-prepend 2 set policy-options policy-statement Direct-To-BGP term 10 then accept set policy-options policy-statement Direct-To-BGP term 999 then reject set protocols bgp group ISP-AS100 export Direct-To-BGP
IBGP Session between CE devices
- On CE-2, setup IBGP Session with CE-1
set policy-options policy-statement NextHopSelf term one then next-hop self set protocols bgp group IBGP export NextHopSelf set protocols bgp group IBGP type internal set protocols bgp group IBGP local-address 120.0.30.2 set protocols bgp group IBGP authentication-key "$9$3Uey/A0EclLxdBIxdbsJZn/C" set protocols bgp group IBGP export NextHopSelf set protocols bgp group IBGP neighbor 120.0.30.3
You might have noticed that we are using internal interface IP as Router-ID and IBGP neighbor source. At a first glance, this might contradict a typical best practice recommendation of using router’s loopback address for this function. In our example, Loopback peering would not improve network stability, but introduce unnecessary complexity. Loopback peering is only required if you have multiple L3 paths interconnecting your CE devices. Those are not present in our example.
Please note, that we are using Next-Hop-Self on our IBGP session. Refer to ‘Next-Hop-Self Explained’ article if you are not familiar with the concept.
- On CE-2, setup IBGP Session with CE-1
set policy-options policy-statement NextHopSelf term one then next-hop self set protocols bgp group IBGP type internal set protocols bgp group IBGP local-address 120.0.30.3 set protocols bgp group IBGP authentication-key "$9$tEpy01hevLVwgSrwgoJHkp0B" set protocols bgp group IBGP export NextHopSelf set protocols bgp group IBGP neighbor 120.0.30.2
CE-1 BGP Verification
- Verify that the default route 0.0.0.0/0 is being received from the ISP
> show route receive-protocol bgp 120.0.4.9 inet.0: 9 destinations, 9 routes (9 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path * 0.0.0.0/0 120.0.4.9 100 I
- Verify that the default route got installed into the routing table
> show route 0.0.0.0 inet.0: 9 destinations, 9 routes (9 active, 0 holddown, 0 hidden) + = Active Route, - = Last Active, * = Both 0.0.0.0/0 *[BGP/170] 4d 20:07:14, localpref 120 AS path: 100 I > to 120.0.4.9 via ge-0/0/1.0
- Verify that the default route is being re-advertised to CE2 via IBGP session with LP=120
> show route advertising-protocol bgp 120.0.30.3 inet.0: 9 destinations, 9 routes (9 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path * 0.0.0.0/0 Self 120 100 I
- Verify that your network prefix (120.0.30/24) is being advertised to the ISP
> show route advertising-protocol bgp 120.0.4.9 inet.0: 9 destinations, 9 routes (9 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path * 120.0.30.0/24 Self I
CE-2 BGP Verification
- Verify that the default route 0.0.0.0/0 is being received from the ISP
> show route receive-protocol bgp 120.0.4.13 inet.0: 7 destinations, 8 routes (7 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path 0.0.0.0/0 120.0.4.13 100 I
- Verify that the default route is being received via IBGP from CE-1 with LP=120
> show route receive-protocol bgp 120.0.30.2 inet.0: 7 destinations, 8 routes (7 active, 0 holddown, 0 hidden) Prefix Nexthop MED Lclpref AS path * 0.0.0.0/0 120.0.30.2 120 100 I
- Verify that the default route got installed into the routing table. It should be pointing to CE-1
> show route 0.0.0.0 inet.0: 7 destinations, 8 routes (7 active, 0 holddown, 0 hidden) + = Active Route, - = Last Active, * = Both 0.0.0.0/0 *[BGP/170] 4d 20:14:17, localpref 120 AS path: 100 I > to 120.0.30.2 via ge-0/0/2.0 [BGP/170] 4d 21:23:36, localpref 100 AS path: 100 I > to 120.0.4.13 via ge-0/0/1.0
- Verify that your network prefix (120.0.30/24) is being advertised to the ISP with AS-Prepend
> show route advertising-protocol bgp 120.0.4.13 Prefix Nexthop MED Lclpref AS path * 120.0.30.0/24 Self 2 [65001] I
VRRP Configuration and Verification
- CE-1 with high priority
set interfaces ge-0/0/2 description "LAN Segment" set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.2/24 vrrp-group 1 virtual-address 120.0.30.1 set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.2/24 vrrp-group 1 priority 120 set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.2/24 vrrp-group 1 preempt set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.2/24 vrrp-group 1 accept-data
- On CE-1, configure interface tracking to decrease VRRP priority in case of CE-1 to PE-1 link failure
set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.2/24 vrrp-group 1 track interface ge-0/0/1 priority-cost 50
- CE-2 with low priority
set interfaces ge-0/0/2 description "LAN Segment" set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.3/24 vrrp-group 1 virtual-address 120.0.30.1 set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.3/24 vrrp-group 1 priority 100 set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.3/24 vrrp-group 1 preempt set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.3/24 vrrp-group 1 accept-data
· Verify VRRP status on CE-1 and CE-2
> show vrrp brief Interface State Group VR state VR Mode Timer Type Address ge-0/0/2.0 up 1 master Active A 0.514 lcl 120.0.30.2 vip 120.0.30.1 > show vrrp brief Interface State Group VR state VR Mode Timer Type Address ge-0/0/2.0 up 1 backup Active D 3.582 lcl 120.0.30.3 vip 120.0.30.1 mas 120.0.30.2
CE1 Complete Configuration
set system host-name CE-1 set system domain-name bgphelp.com set system time-zone America/New_York set system no-redirects set system root-authentication encrypted-password <REMOVED> set system name-server 120.0.30.10 set system login user bgphelp uid 2000 set system login user bgphelp class super-user set system login user bgphelp authentication encrypted-password <REMOVED> set system services ssh protocol-version v2 set system services netconf ssh set system syslog user * any emergency set system syslog host 120.0.30.10 any info set system syslog file messages any any set system syslog file messages authorization info set system syslog file interactive-commands interactive-commands any set system ntp server 120.0.30.10 set interfaces ge-0/0/1 description "CE1->PE2" set interfaces ge-0/0/1 unit 0 family inet filter input-list discard-martian set interfaces ge-0/0/1 unit 0 family inet filter input-list discard-local set interfaces ge-0/0/1 unit 0 family inet filter input-list accept-any set interfaces ge-0/0/1 unit 0 family inet filter output-list accept-local set interfaces ge-0/0/1 unit 0 family inet filter output-list discard-any set interfaces ge-0/0/1 unit 0 family inet address 120.0.4.10/30 set interfaces ge-0/0/2 description "LAN Segment" set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.2/24 vrrp-group 1 virtual-address 120.0.30.1 set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.2/24 vrrp-group 1 priority 120 set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.2/24 vrrp-group 1 preempt set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.2/24 vrrp-group 1 accept-data set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.2/24 vrrp-group 1 track interface ge-0/0/1 priority-cost 50 set interfaces lo0 unit 0 family inet filter input-list accept-protocols set interfaces lo0 unit 0 family inet filter input-list accept-management set interfaces lo0 unit 0 family inet filter input-list accept-monitoring set interfaces lo0 unit 0 family inet filter input-list discard-any set snmp location MarsDC:BAY12334:U123 set snmp contact "IP NOC 1-345-12-1234" set snmp community f0ryoureyesonly clients 120.0.30.10/32 set snmp trap-group all version v2 set snmp trap-group all targets 120.0.30.10 set routing-options router-id 120.0.30.2 set routing-options autonomous-system 65001 set protocols bgp log-updown set protocols bgp group ISP-AS100 type external set protocols bgp group ISP-AS100 import Default set protocols bgp group ISP-AS100 authentication-key "$9$9UPDt0IylMNdsEcds24DjCtu" set protocols bgp group ISP-AS100 export Direct-To-BGP set protocols bgp group ISP-AS100 peer-as 100 set protocols bgp group ISP-AS100 neighbor 120.0.4.9 description "ISP FastAccess: Circuit GD8AJ12B: ISP NOC 800-111-2222" set protocols bgp group IBGP type internal set protocols bgp group IBGP local-address 120.0.30.2 set protocols bgp group IBGP authentication-key "$9$3Uey/A0EclLxdBIxdbsJZn/C" set protocols bgp group IBGP export NextHopSelf set protocols bgp group IBGP neighbor 120.0.30.3 set policy-options prefix-list LocallyOriginated 120.0.30.0/24 set policy-options prefix-list Default 0.0.0.0/0 set policy-options policy-statement Default term 10 from prefix-list Default set policy-options policy-statement Default term 10 then local-preference 120 set policy-options policy-statement Default term 10 then accept set policy-options policy-statement Default term 999 then reject set policy-options policy-statement Direct-To-BGP term 10 from protocol direct set policy-options policy-statement Direct-To-BGP term 10 from prefix-list LocallyOriginated set policy-options policy-statement Direct-To-BGP term 10 then accept set policy-options policy-statement Direct-To-BGP term 999 then reject set policy-options policy-statement NextHopSelf term one then next-hop self set firewall family inet filter discard-martian term rfc919 from source-address 255.255.255.255/32 set firewall family inet filter discard-martian term rfc919 then discard set firewall family inet filter discard-martian term rfc1122 from source-address 0.0.0.0/8 set firewall family inet filter discard-martian term rfc1122 from source-address 127.0.0.0/8 set firewall family inet filter discard-martian term rfc1122 from source-address 240.0.0.0/4 set firewall family inet filter discard-martian term rfc1122 then discard set firewall family inet filter discard-martian term rfc1918 from source-address 10.0.0.0/8 set firewall family inet filter discard-martian term rfc1918 from source-address 172.16.0.0/12 set firewall family inet filter discard-martian term rfc1918 from source-address 192.168.0.0/16 set firewall family inet filter discard-martian term rfc1918 then discard set firewall family inet filter discard-martian term rfc2544 from source-address 198.18.0.0/15 set firewall family inet filter discard-martian term rfc2544 then discard set firewall family inet filter discard-martian term rfc3171 from source-address 224.0.0.0/4 set firewall family inet filter discard-martian term rfc3171 then discard set firewall family inet filter discard-martian term rfc3927 from source-address 169.254.0.0/16 set firewall family inet filter discard-martian term rfc3927 then discard set firewall family inet filter discard-martian term rfc5736 from source-address 192.0.0.0/24 set firewall family inet filter discard-martian term rfc5736 then discard set firewall family inet filter discard-martian term rfc5737 from source-address 192.0.2.0/24 set firewall family inet filter discard-martian term rfc5737 from source-address 198.51.100.0/24 set firewall family inet filter discard-martian term rfc5737 from source-address 203.0.113.0/24 set firewall family inet filter discard-martian term rfc5737 then discard set firewall family inet filter discard-martian term rfc6598 from source-address 100.64.0.0/10 set firewall family inet filter discard-martian term rfc6598 then discard set firewall family inet filter discard-local term 10 from source-address 120.0.30.0/24 set firewall family inet filter discard-local term 10 then discard set firewall family inet filter accept-any term 10 then accept set firewall family inet filter accept-local term 10 from source-address 120.0.30.0/24 set firewall family inet filter accept-local term 10 then accept set firewall family inet filter accept-local term 20 from source-address 120.0.4.10/32 set firewall family inet filter accept-local term 20 then accept set firewall family inet filter discard-any term 10 then discard set firewall family inet filter accept-protocols term bgp from source-address 120.0.4.9/32 set firewall family inet filter accept-protocols term bgp from source-address 120.0.30.3/32 set firewall family inet filter accept-protocols term bgp from protocol tcp set firewall family inet filter accept-protocols term bgp from port bgp set firewall family inet filter accept-protocols term bgp then accept set firewall family inet filter accept-management term ssh from source-address 120.0.30.10/32 set firewall family inet filter accept-management term ssh from source-address 192.168.3.0/24 set firewall family inet filter accept-management term ssh from protocol tcp set firewall family inet filter accept-management term ssh from port ssh set firewall family inet filter accept-management term ssh then accept set firewall family inet filter accept-management term snmp from source-address 120.0.30.10/32 set firewall family inet filter accept-management term snmp from protocol udp set firewall family inet filter accept-management term snmp from destination-port snmp set firewall family inet filter accept-management term snmp then accept set firewall family inet filter accept-management term ntp from source-address 120.0.30.10/32 set firewall family inet filter accept-management term ntp from protocol udp set firewall family inet filter accept-management term ntp from port ntp set firewall family inet filter accept-management term ntp then accept set firewall family inet filter accept-management term dns from source-address 120.0.30.10/32 set firewall family inet filter accept-management term dns from protocol udp set firewall family inet filter accept-management term dns from protocol tcp set firewall family inet filter accept-management term dns from source-port 53 set firewall family inet filter accept-management term dns then accept set firewall family inet filter accept-management term netconf from source-address 120.0.30.10/32 set firewall family inet filter accept-management term netconf from source-address 192.168.3.0/24 set firewall family inet filter accept-management term netconf from protocol tcp set firewall family inet filter accept-management term netconf from destination-port 830 set firewall family inet filter accept-management term netconf then accept set firewall family inet filter accept-monitoring term icmp from protocol icmp set firewall family inet filter accept-monitoring term icmp from icmp-type echo-reply set firewall family inet filter accept-monitoring term icmp from icmp-type echo-request set firewall family inet filter accept-monitoring term icmp from icmp-type time-exceeded set firewall family inet filter accept-monitoring term icmp from icmp-type unreachable set firewall family inet filter accept-monitoring term icmp from icmp-type source-quench set firewall family inet filter accept-monitoring term icmp from icmp-type router-advertisement set firewall family inet filter accept-monitoring term icmp from icmp-type parameter-problem set firewall family inet filter accept-monitoring term icmp then accept set firewall family inet filter accept-monitoring term traceroute-udp from protocol udp set firewall family inet filter accept-monitoring term traceroute-udp from destination-port 33435-33450 set firewall family inet filter accept-monitoring term traceroute-udp then accept
CE2 Complete Configuration
Repetitive elements removed
set system host-name CE-2 set system root-authentication encrypted-password <REMOVED> set system services ssh set system services netconf ssh set interfaces ge-0/0/1 description "'CE4->PE2'" set interfaces ge-0/0/1 unit 0 family inet address 120.0.4.14/30 set interfaces ge-0/0/2 description "LAN Segment" set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.3/24 vrrp-group 1 virtual-address 120.0.30.1 set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.3/24 vrrp-group 1 priority 100 set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.3/24 vrrp-group 1 preempt set interfaces ge-0/0/2 unit 0 family inet address 120.0.30.3/24 vrrp-group 1 accept-data set routing-options router-id 120.0.30.3 set routing-options autonomous-system 65001 set routing-options resolution set protocols bgp group ISP-AS100 type external set protocols bgp group ISP-AS100 import Default set protocols bgp group ISP-AS100 authentication-key "$9$9UPDt0IylMNdsEcds24DjCtu" set protocols bgp group ISP-AS100 export Direct-To-BGP set protocols bgp group ISP-AS100 peer-as 100 set protocols bgp group ISP-AS100 neighbor 120.0.4.13 description "ISP FastAccess: Circuit GD8AJ12C: ISP NOC 800-111-2222" set protocols bgp group IBGP type internal set protocols bgp group IBGP local-address 120.0.30.3 set protocols bgp group IBGP authentication-key "$9$tEpy01hevLVwgSrwgoJHkp0B" set protocols bgp group IBGP export NextHopSelf set protocols bgp group IBGP neighbor 120.0.30.2 set policy-options prefix-list LocallyOriginated 120.0.30.0/24 set policy-options prefix-list Default 0.0.0.0/0 set policy-options policy-statement Default term 10 from prefix-list Default set policy-options policy-statement Default term 10 then local-preference 100 set policy-options policy-statement Default term 10 then accept set policy-options policy-statement Default term 999 then reject set policy-options policy-statement Direct-To-BGP term 10 from protocol direct set policy-options policy-statement Direct-To-BGP term 10 from prefix-list LocallyOriginated set policy-options policy-statement Direct-To-BGP term 10 then as-path-prepend 2 set policy-options policy-statement Direct-To-BGP term 10 then accept set policy-options policy-statement Direct-To-BGP term 999 then reject set policy-options policy-statement NextHopSelf term one then next-hop self
